Our Products & Services
1, AI Consultancy as a Service (AIcaaS)
We offer AI consultancy as a service (AIcaaS) product offers businesses expert guidance and end-to-end support for their artificial intelligence initiatives on a flexible, cloud-based model. It is designed for companies that lack in-house AI expertise, infrastructure, or a clear strategy for leveraging AI effectively. This product extends beyond generic AI offerings, combining strategic consulting with technical implementation and management.
Key components of an AIcaaS product
An AIcaaS offering typically provides a comprehensive suite of services that guide a customer from identifying a business challenge to deploying and scaling an AI solution.
1. Strategic consulting and planning
- AI readiness assessment: Evaluates a company's data, technology, and talent to identify its capacity for AI adoption.
- Opportunity mapping: Pinpoints specific business problems that AI can solve to maximize return on investment (ROI).
- Roadmap development: Creates a phased plan for implementing AI that aligns with the client's business goals and resources.
2. Data management and engineering
- Data audit and preparation: Ensures the client has high-quality, clean, and well-organized data for training and running AI models.
- Data governance: Establishes a framework for managing data privacy, security, and ethical use in compliance with regulations like GDPR or HIPAA.
- MLOps setup: Designs and implements a machine learning operations infrastructure to manage the full AI lifecycle, from data ingestion to model deployment.
3. AI model development and deployment
- Model design and training: Develops custom machine learning or generative AI models tailored to the client's specific needs.
- Prototyping (PoC): Builds and tests a small-scale proof-of-concept to validate the technical feasibility and business value of a solution before a full-scale investment.
- Integration: Deploys AI solutions and integrates them seamlessly with the client's existing business systems, such as CRM and ERP platforms.
4. Ongoing support and optimization
- Model monitoring: Continuously monitors AI models in production to ensure they maintain performance and accuracy over time.
- Optimization and scaling: Enhances and scales AI models and infrastructure as the business grows and needs evolve.
- Training and enablement: Trains internal teams on how to use and manage the new AI systems, fostering self-sufficiency and ensuring sustainable value.
Benefits of an AIcaaS product
AIcaaS offers a compelling value proposition by providing companies with the advanced capabilities of AI without the traditional barriers of entry.
- Cost efficiency: Reduces the need for significant upfront investment in AI infrastructure, hardware, and hiring specialized data scientists.
- Accelerated time-to-value: Enables companies to implement AI solutions and start realizing benefits much faster than with in-house development.
- Access to expertise: Provides access to specialized AI consultants who bring broad cross-industry experience and technical knowledge.
- Risk mitigation: Reduces the high risk of failure associated with internal AI projects by relying on proven methodologies and expert guidance.
- Scalability: Allows businesses to start with smaller projects and scale their AI capabilities dynamically as their needs and budget expand.
- Focus on core business: Frees up a company's internal teams to focus on their primary business objectives, delegating the technical complexity of AI to the service provider.
AIcaaS vs. AI as a service (AIaaS)
While often used interchangeably, AIcaaS is distinct from standard AIaaS (e.g., cloud provider APIs) in the level of human involvement and customization.
Aspect
AIcaaS (Consultancy as a Service)
AIaaS (AI as a Service)
Primary focus
Customized strategy and end-to-end solution development tailored to specific business goals.
Access to pre-built, ready-to-use AI models and APIs via a cloud subscription.
Engagement
Human-led, high-touch partnership that involves assessment, planning, and implementation by AI consultants.
Technology-driven access that allows a company's developers to plug into a provider's services.
Technical expertise
Consultants provide the deep expertise needed for complex integration and custom model training.
Lower technical expertise is needed to use the APIs, but less customization is possible with pre-built models.
Value delivered
A strategic business outcome (e.g., a roadmap, process automation, or custom generative AI).
A specific AI function (e.g., natural language processing, a chatbot).
2, ServiceNow Implementation as a Service
Implementation as a service for ServiceNow refers to an engagement model where a third-party partner provides end-to-end services to deploy, configure, and manage a ServiceNow solution. This model uses the provider's expertise and methodologies to streamline the process, often leading to a faster and more efficient implementation than attempting it with in-house resources alone.
Key components of implementation as a service
Reputable ServiceNow partners offer a comprehensive suite of services that follow the platform's standard methodologies, such as Now Create.
- Consulting and strategy: Experts work with your business to define goals, map a strategic roadmap, and identify which ServiceNow modules are most appropriate for your needs, such as IT Service Management (ITSM) or HR Service Delivery (HRSD).
- Design and configuration: Partners design user-focused solutions and configure the platform to your specific business requirements, ensuring maximum use of out-of-the-box functionality to simplify future maintenance.
- Customization and integration: For unique requirements, partners develop custom applications and integrate ServiceNow with your existing third-party systems like enterprise resource planning (ERP) or customer relationship management (CRM).
- Data migration: Service providers handle the complex process of securely migrating your organization's data from legacy systems to the new ServiceNow instance.
- Testing and quality assurance: Rigorous testing is performed at every stage, including unit testing, integration testing, and user acceptance testing (UAT), to ensure a smooth go-live.
- Deployment and training: Experts manage the deployment and provide comprehensive training to ensure your users and administrators adopt the new system effectively.
- Post-launch support and optimization: A partner's role often extends beyond the initial launch to provide ongoing support, maintenance, and optimization services.
Benefits of this service model
Leveraging a specialized partner for ServiceNow implementation offers significant advantages over a DIY approach.
- Faster time-to-value: Partners use repeatable methodologies and pre-built components to accelerate implementation, allowing your organization to realize a return on its investment much faster.
- Expert guidance: You get access to highly skilled, certified ServiceNow experts who have experience with a wide variety of implementations. This helps you avoid common pitfalls and reduces technical debt.
- Reduced risk: An experienced partner assumes accountability for the project's success, with strong governance, comprehensive testing protocols, and robust risk management practices.
- Increased efficiency and ROI: By streamlining workflows and automating manual tasks, the implementation service boosts productivity and lowers operational costs.
- Enhanced user adoption: Partners create strategies for change management and provide structured, role-based training to ensure employees embrace and effectively use the new platform.
- Scalability: The implementation is built with long-term growth in mind, creating a solution that can easily expand to accommodate new business needs and additional ServiceNow modules.
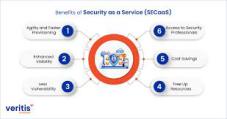
3, Cybersecurity as a Service (CSaaS)
Cybersecurity as a Service (CSaaS) is an outsourced model where a third-party vendor provides and manages your organization's security posture on a subscription or "pay-as-you-go" basis, often leveraging a cloud-based platform and a dedicated Security Operations Center (SOC).
The offerings are typically broad and scalable, designed to give you access to expert-level security without the need for a large in-house team or significant upfront investment.
Key services commonly offered in a CSaaS model include:
1. Threat Monitoring and Management
Managed Detection and Response (MDR): 24/7/365 monitoring, threat hunting, and rapid response to security incidents across endpoints, network, and cloud environments.
Security Information and Event Management (SIEM) as a Service: Collecting, analyzing, and correlating security data and logs from across your systems in real-time to detect threats and manage compliance.
Vulnerability Management: Continuous scanning and auditing to identify vulnerabilities in software, hardware, and processes, often followed by patch management and remediation guidance.
2. Security Infrastructure and Protection
Endpoint Protection/EDR (Endpoint Detection and Response): Protecting devices like laptops, desktops, and mobile devices from malware, ransomware, and other threats.
Network Security: Services like Firewall as a Service (FWaaS), Intrusion Detection/Prevention Systems (IDPS), and Distributed Denial of Service (DDoS) protection.
Cloud Security: Securing multi-cloud environments, including security posture management, identity and access, and compliance across platforms like AWS, Azure, and Google Cloud.
Email and Web Security: Protection against spam, phishing, malware, and web-based threats.
3. Identity and Access Control
Identity and Access Management (IAM) as a Service: Managing user identities, permissions, Multi-Factor Authentication (MFA), Single Sign-On (SSO), and role-based access control (RBAC).
4. Risk and Compliance Services
Security Assessments and Audits: Periodic evaluations of your security tools, policies, and posture to ensure they meet industry standards and best practices.
Penetration Testing (Pen Testing): Simulating real-world attacks to find exploitable vulnerabilities in your systems.
Compliance Management: Assisting your organization in meeting specific regulatory requirements like GDPR, HIPAA, or PCI-DSS.
5. Incident Response and Recovery
Incident Response: Immediate containment, investigation, and remediation of active security breaches to minimize impact and restore operations quickly.
Data Loss Prevention (DLP): Tools and policies to monitor, protect, and control sensitive data to prevent unauthorized extraction or sharing.
Disaster Recovery and Business Continuity Planning: Strategies and tools to ensure business-critical systems remain running or can be quickly recovered after an interruption.
A major benefit of CSaaS is the combination of advanced security technology, specialized human expertise, and 24/7 coverage, making enterprise-grade security accessible and cost-effective for businesses of all sizes.
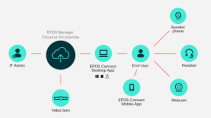
4, ePOS Systems deployment and Maintenance
As a managed service, ePOS deployment and maintenance provide businesses with a hands-off approach to managing their electronic point of sale systems. Instead of handling the complex setup, configuration, and ongoing support internally, companies outsource these tasks to a third-party provider, allowing them to focus on core business operations.
Managed ePOS services offer a comprehensive solution covering both the initial installation and the entire lifecycle of the system. This model is particularly beneficial for multi-site businesses or those in the hospitality and retail sectors where reliable and efficient transaction processing is critical.
Key components of ePOS managed services
Deployment as a service
This component handles the initial rollout of your ePOS infrastructure, ensuring a smooth transition with minimal disruption to your business.
- Project management: A dedicated project manager coordinates all aspects of the deployment, including logistics, scheduling, and communication.
- Configuration and installation: Service providers install and set up all hardware (terminals, printers, card readers) and software, including customizing the system to fit the business's specific needs, such as menus or product lists.
- Software and data setup: This includes installing the ePOS software, configuring the back-office management system, and migrating critical data like product information, pricing, and customer loyalty programs.
- Training: Onsite training is provided to staff to ensure they can confidently use the new system from day one.
Benefits for businesses
|
Aspect |
Benefit of managed ePOS services |
|
Time and cost savings |
Reduces the need for an in-house IT team, cuts costs associated with emergency repairs, and provides predictable monthly expenses through a subscription-based model. |
|
Increased reliability |
Proactive maintenance and rapid-response support minimize system downtime, ensuring transactions and daily operations run smoothly and preventing lost sales and frustrated customers. |
|
Enhanced security |
Managed services include the latest security features, software updates, and compliance support, protecting businesses from data breaches and fraud. |
|
Improved efficiency |
Automated updates, remote management, and staff training help to streamline operations and reduce human errors. |
|
Scalability and flexibility |
A service-based model allows businesses to scale up or down as needed. Cloud-based ePOS systems enable remote management across multiple locations and offer flexibility with hardware options. |
|
Data and insights |
Service providers often include access to reporting and analytics features, which offer valuable insights into sales, inventory, and customer behavior to help drive business decisions. |
- Proactive and preventative maintenance: Scheduled health checks, hardware diagnostics, and software updates are performed regularly to keep the systems in optimal condition. This approach prevents problems from occurring, which is more cost-effective than reactive repairs.
- Break-fix support: In the event of a hardware or software failure, an engineer can be dispatched to resolve the issue onsite. Many providers also offer "loan stock" to ensure operations can continue while a device is being repaired.
- Security management: The service includes deploying security patches, ensuring compliance with standards like PCI DSS, and protecting sensitive customer and transaction data.
- Helpdesk and technical support: Businesses have access to a support team to address any hardware or software issues. Support can be offered remotely or via on-site visits.
Maintenance as a service
Once deployed, the provider takes over the day-to-day management and support of the ePOS system, ensuring maximum uptime and efficiency.
Remote monitoring and management (RMM): Providers use RMM tools to monitor system performance and identify potential issues before they cause downtime. They can also perform remote software and firmware updates.